
Software Distribution of XML Security Services
The task of Networked Information Systems within the project XML Security Services funded by GBIF-D (BMBF) und SYNTHESYS (EU) is to extend already existent services. The project takes place in cooperation with the Botanical Museum and Botanical Garden Berlin (BGBM) and adds the following features to the current solution:
- user authentication
- role based access control by means of policies
- confidentiality and integrity of transmitted data
- authenticity of the data source
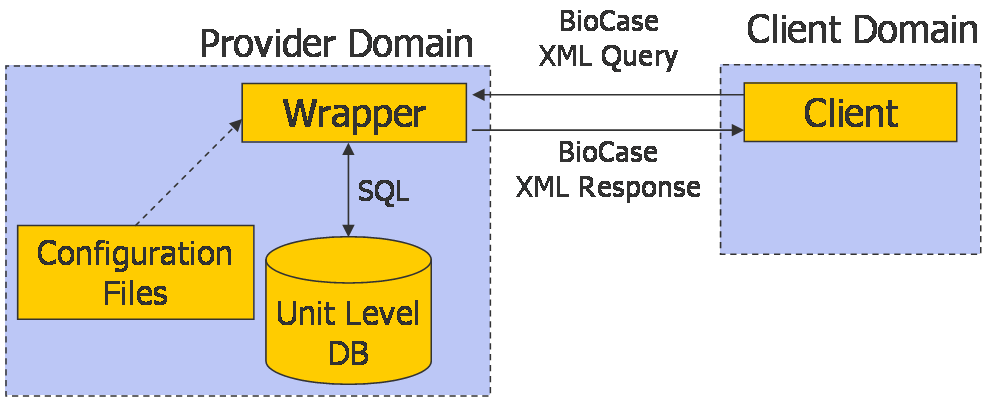
The current BioCASE system architecture
Various providers (mostly botanical museums or institutes) maintain several biodiversity related databases. To support a consistent client access to these databases the BioCASE protocol was developed. Thereby, the databases were encapsulated to the outside world via a wrapper component. The wrapper drives the delivery of XML documents and the BioCASE client communication over the protocol. The BioCASE protocol is XML based and its task mainly consists in exchanging XML data. These XML data is composed of a protocol header and a request or response
Requests may contain different methods as capabilities, scan und search. Capabilities permit to query for specific properties of the provider. Scan lists available documents fo the provider's database. Finally, the most important method Seach supports queries and the delivery of documents.
Besides the header, responses consist of the XML documents to be delivered and may optionally contain diagnostic elements. The latter serve for the transmission of other information like error messages or status codes etc.
Approach XML Security Services
The integration of the XML Security Services was implemented within the BioCASE system architecture by an access control layer situated in front of the actual database provider. This integration base on the XACML standard. A so-called Policy Enforcement Point (PEP) inspects all incoming Http requests for BioCASE protocol elements and enforces role based access control policies defined by the provider.The access control policies determine which BioCASE requests will be blocked and which elements of the content document of a BioCASE response will be filtered out. The assignment of users and roles, as well as the specification of role based access control policies may be established using esspecially developed administration tool called Role Manager besides the provider. The Https- (SSL) protocol is used to realise mutual authentication between a client and the provider's PEP. Therefore, the authentication founds on X.509 certificates, which may be issued using a rudimental Certification Authority (CA) developed on the base of OpenSSL.
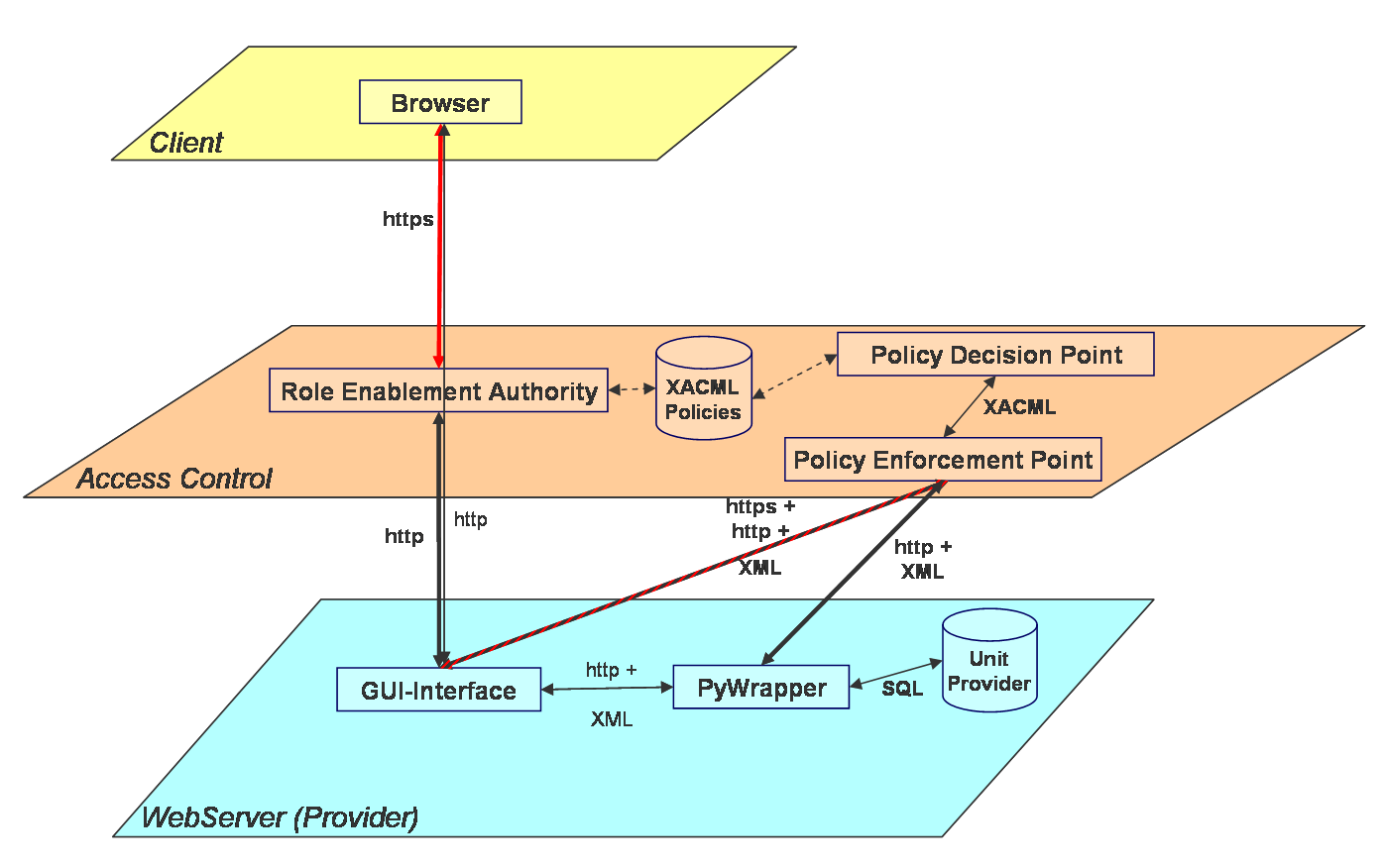
The authenticity of data sources will be ensured by the usage of XML-Signatures. Thereby, the provider may define policies determining those XML elements or element groups to be signed. To support the verification of these XML-Signatures we developed a simple Client-API, reporting the results of the signature verification process within the diagnostic part of the BioCASE response.
Download of the software distribution
The current version of the software distribution may be downloaded from here:XML-Sicherheitsdienste für BioCASE V0.9.0
Documentation
A comprehensive documentation of the software is part of the software distribution's subdirectory doc. There you can also find the JavaDocs of all classes, particularly this of the Client-API (nbi.xmlsec.PEPClient). There are also the following online versions available:The documentation of the Client-API and all java classes Java-Klassen may be also found here:




